Once the server detects a double-spend attempt, it reacts in one of two ways, depending on the transaction state:
- VTXO settled: broadcast forfeit transaction
- VTXO preconfirmed: broadcast checkpoint transaction
Warding Off Griefing Attacks
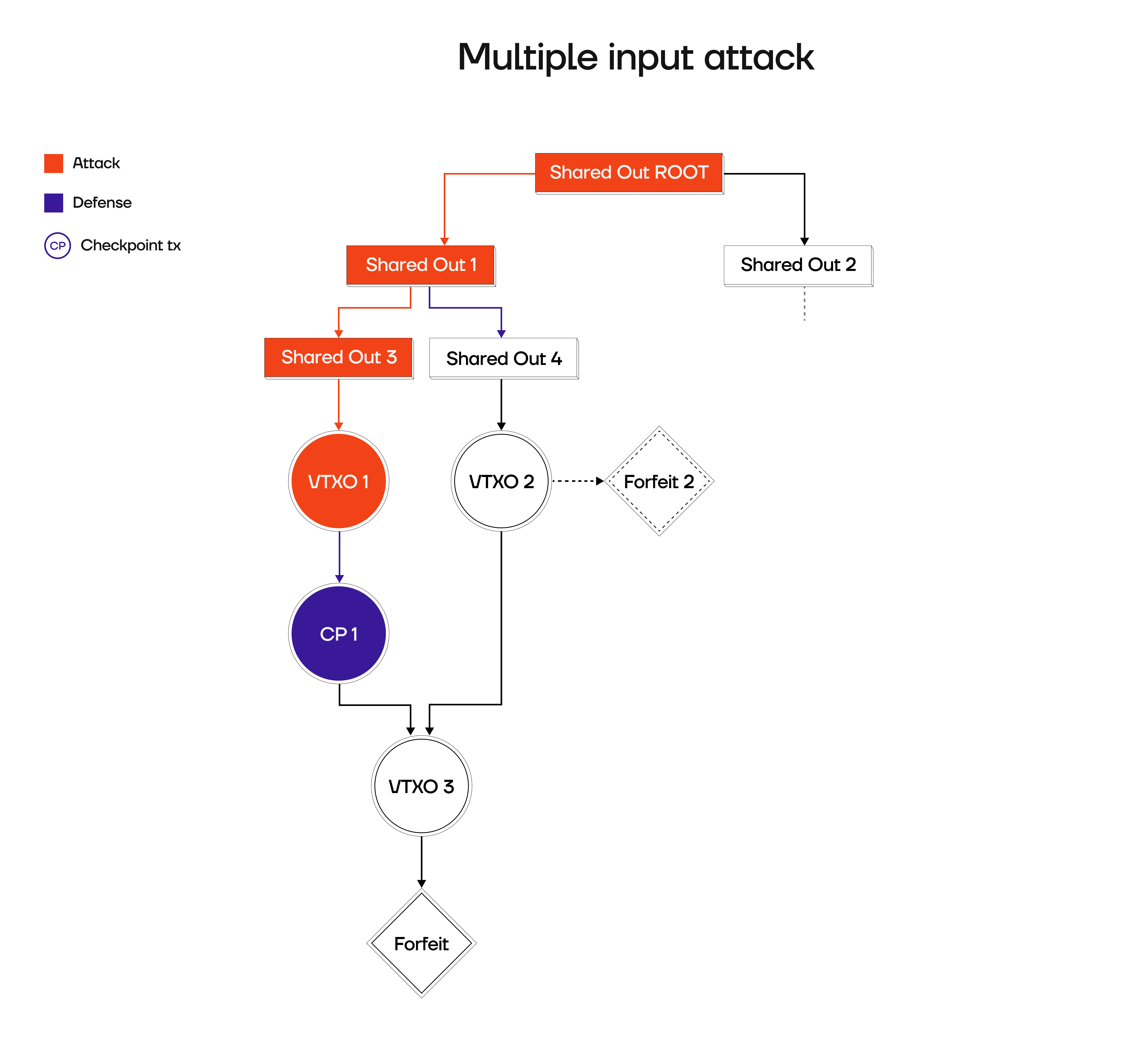
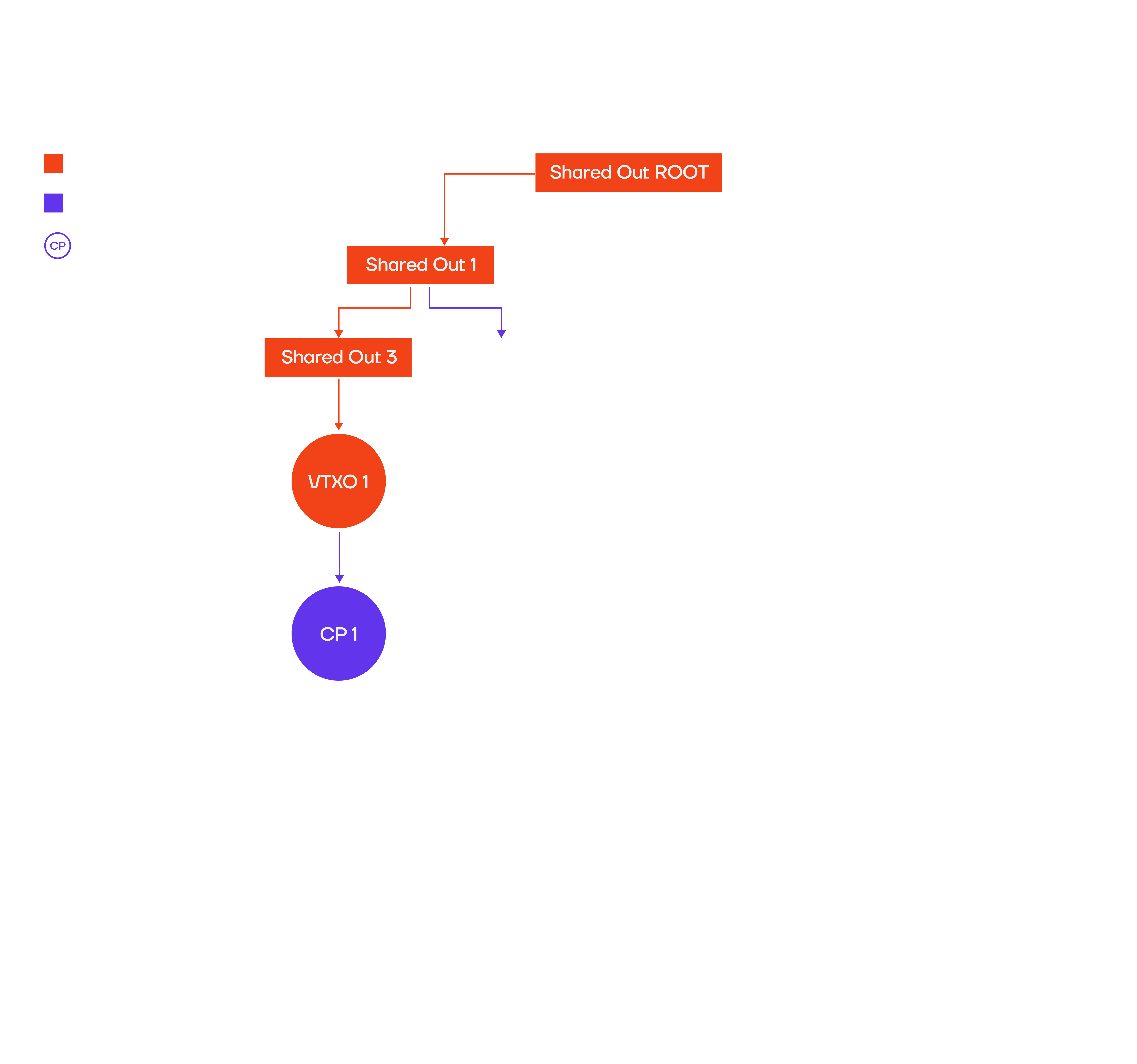
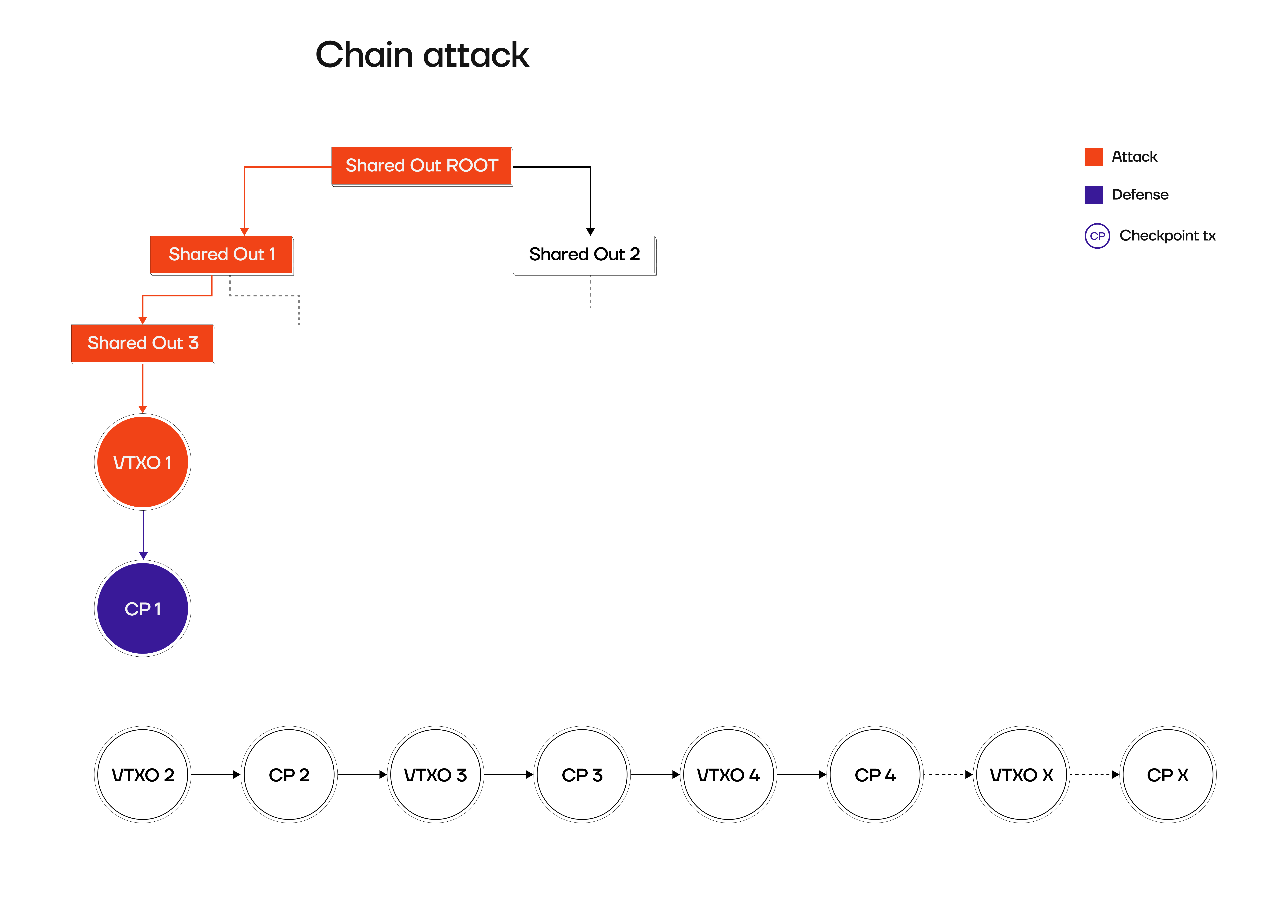
Checkpoint transactions are a core component of the Arkade protocol to ward off potential griefing attacks. They allow the operator to broadcast said transaction when detecting fraudulent user behaviour. A malicious user could chain multiple offchain payments to itself, ultimately batch swap the resulting VTXO or exit the Ark entirely, but then broadcast a unilateral exit path from a prior VTXO of the transaction chain. This attack would force the operator to publish all prior Arkade transactions up to the batch output that anchors them or the unilateral exit, potentially resulting in significant costs.Checkpoint Transaction Structure
A checkpoint transaction is essentially a self-send of the user, but removing the exit script path from the VTXO script leaf, transferring it to the server. It uses a Taproot script with two paths:- A+S (collaborative)
- S+CSV (server after timeout)

Potential Attack Scenarios
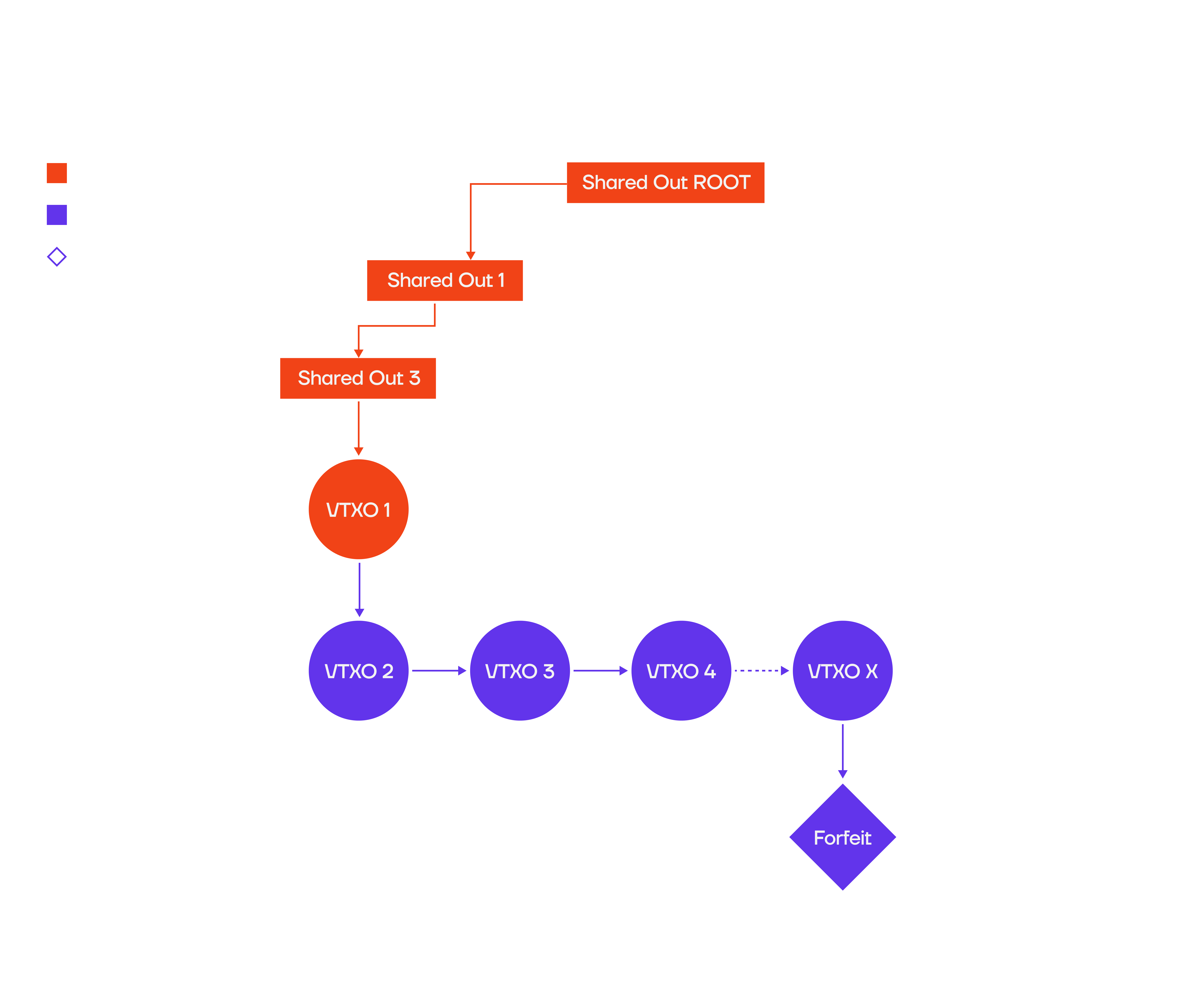
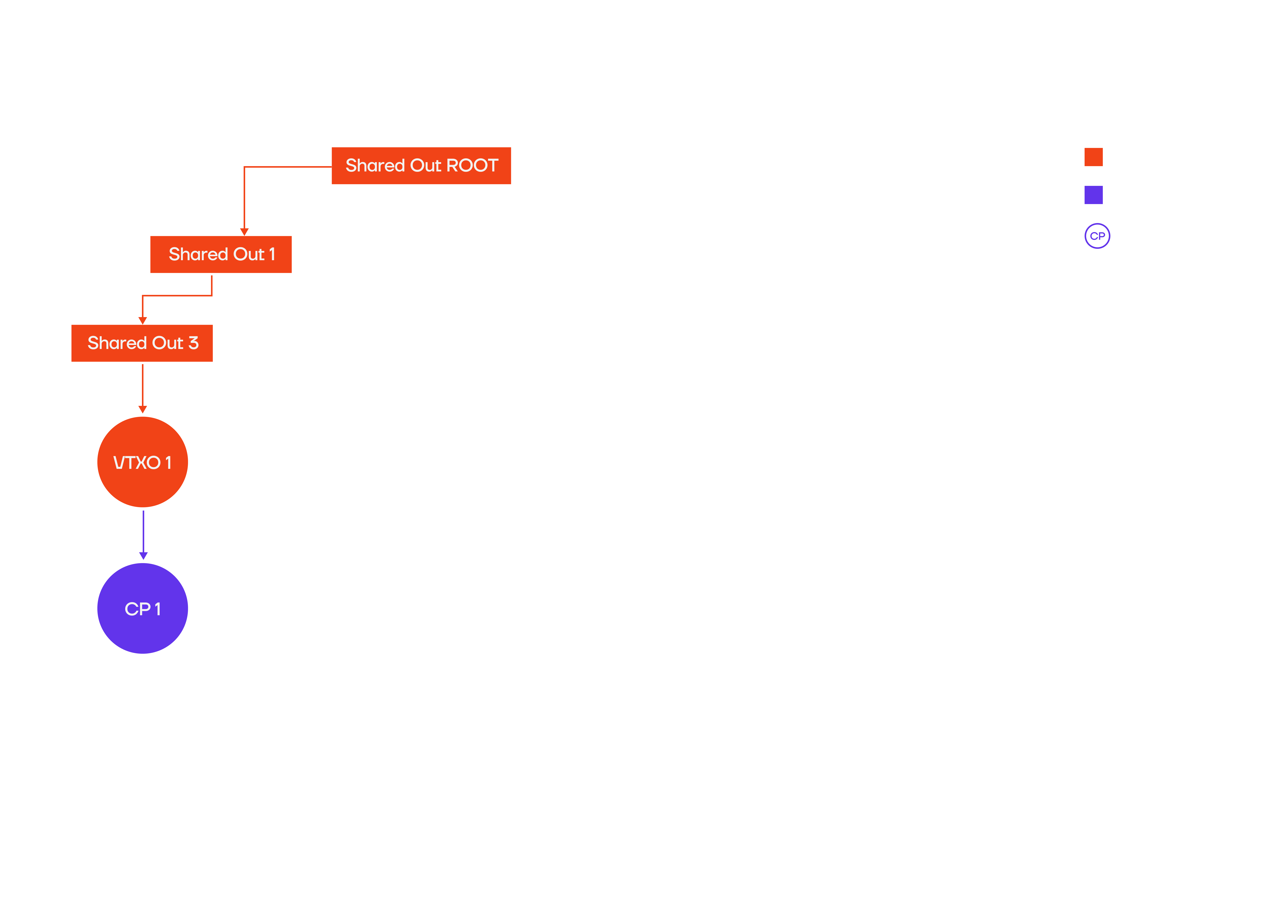
User broadcasts only part of tx chain
One type of attack against the operator could be that a user broadcasts only a part of an offchain transaction chain, (orange) forcing the operator to broadcast all transactions of that chain (violet), resulting in high onchain cost: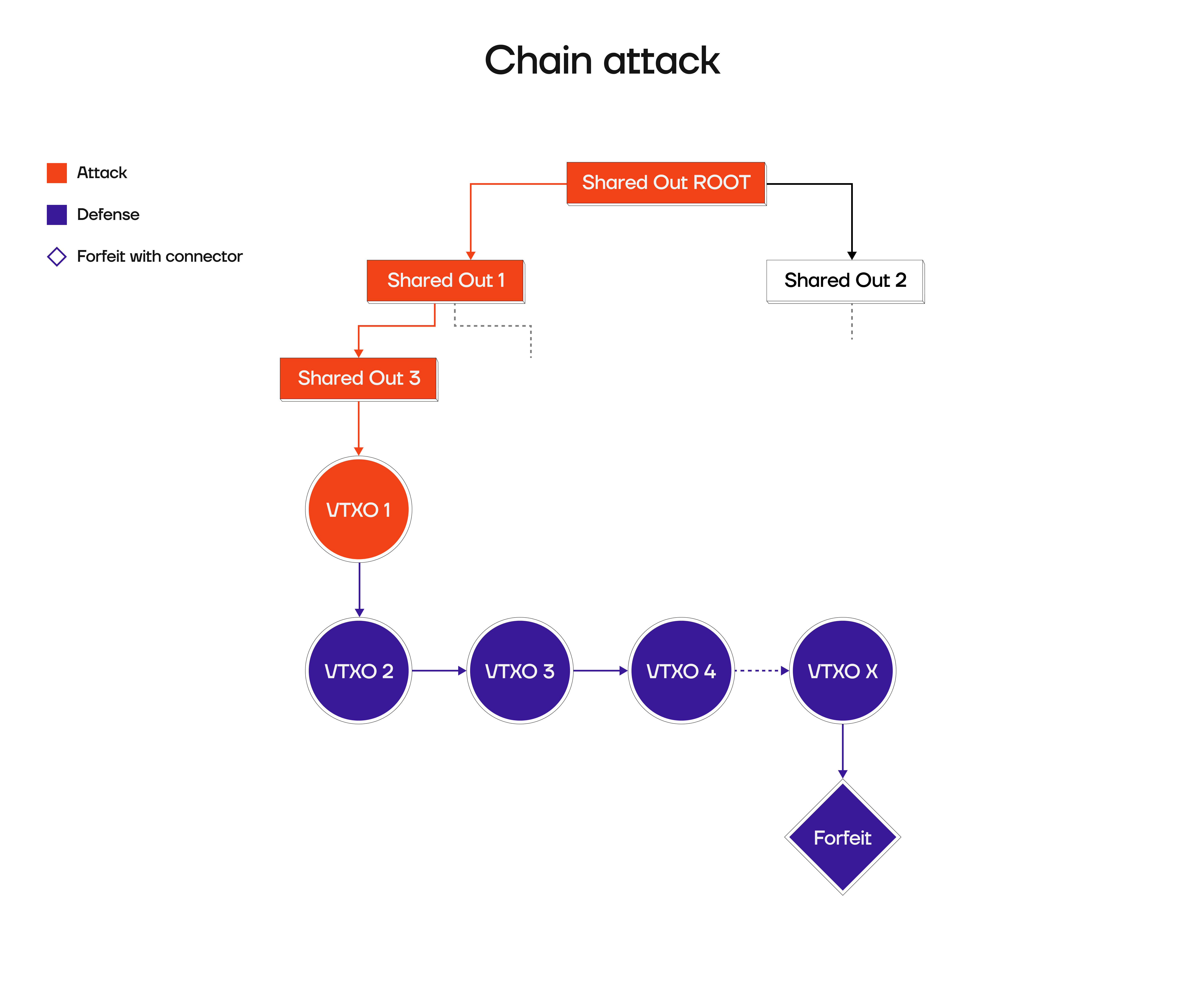
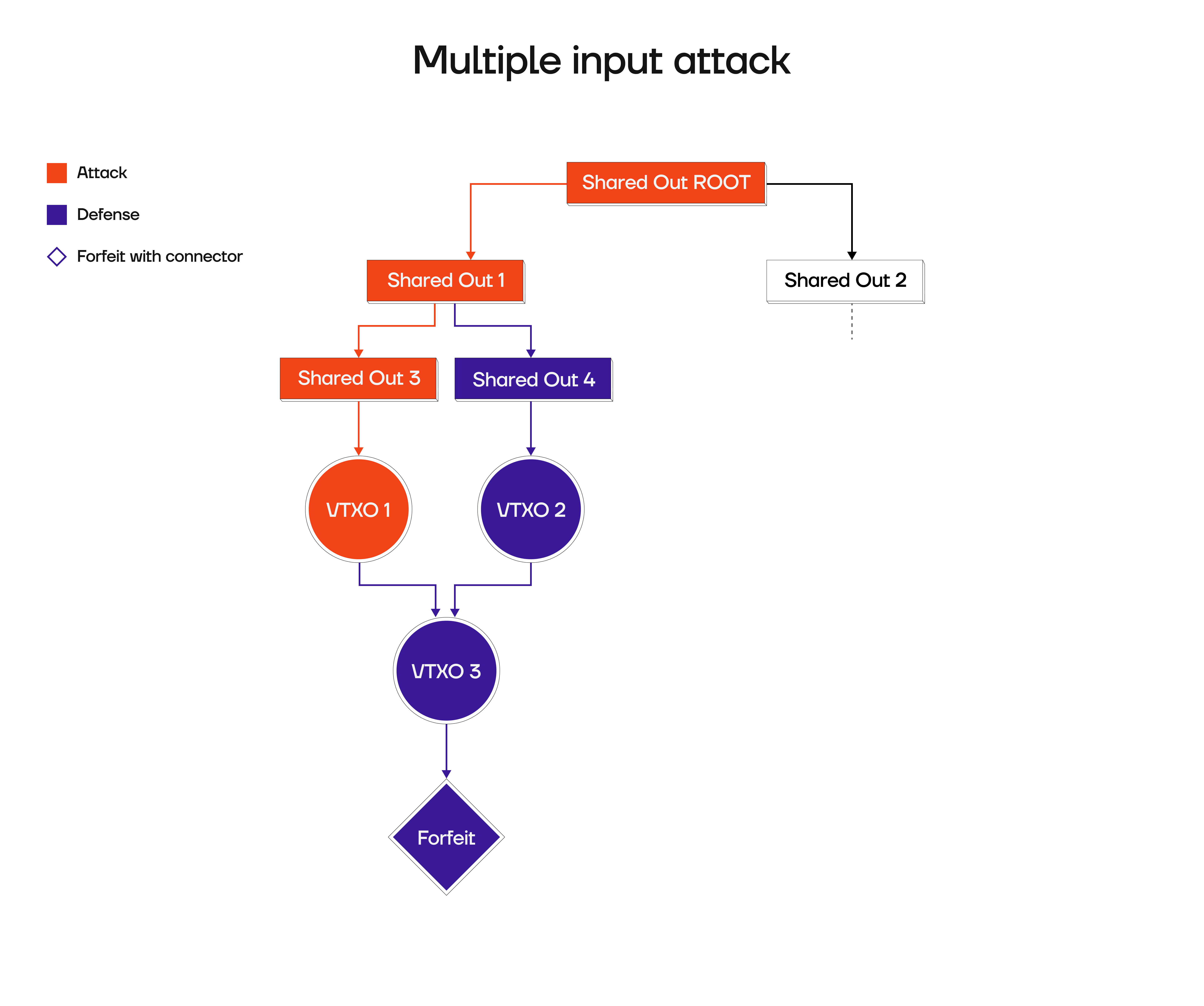
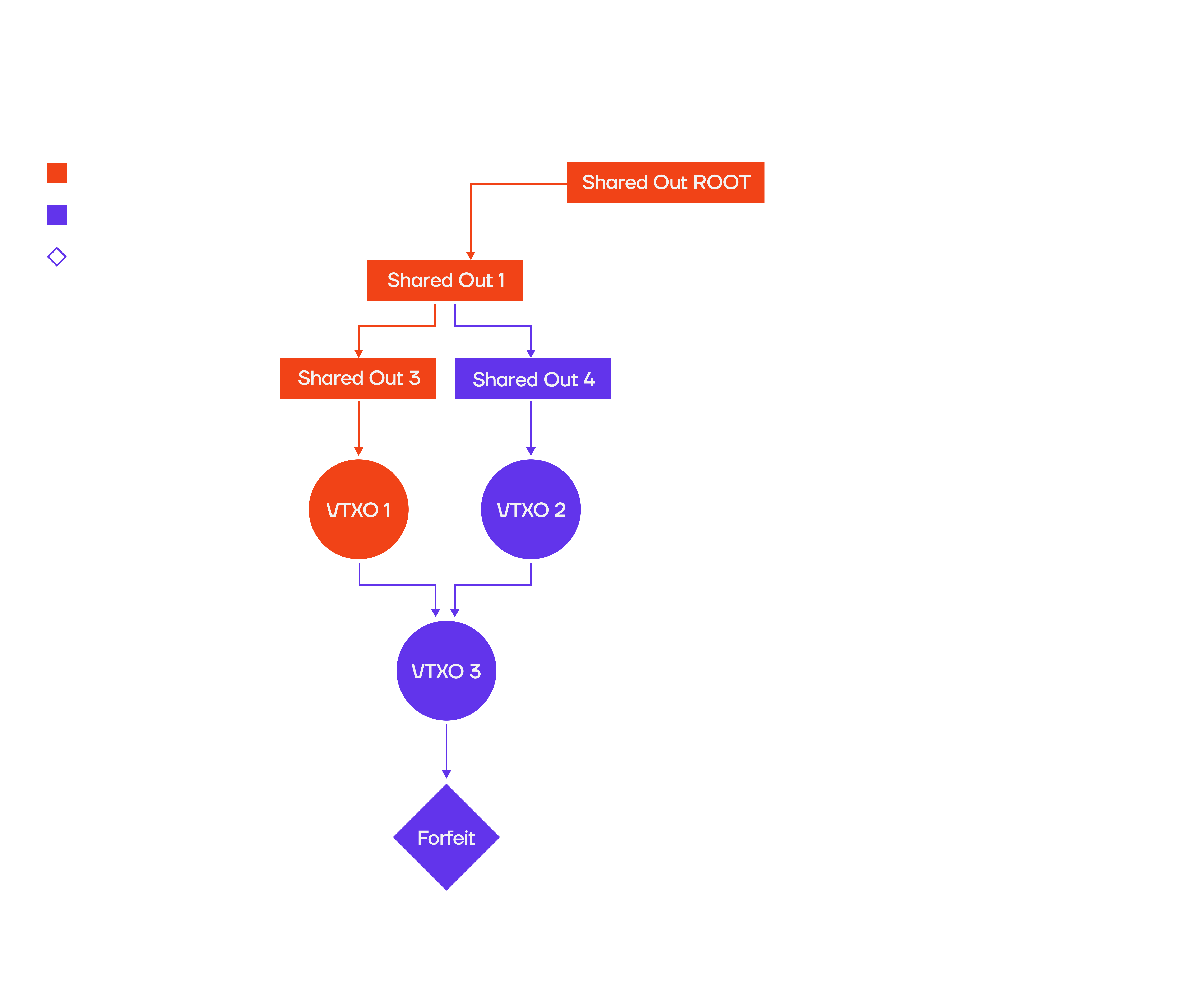
User broadcasts only 1 input of a 2-input tx
Another way to attack the server would be if a user only broadcasts one input of a two-input offchain transaction, forcing the operator to broadcast the second branch of that DAG, resulting in high onchain cost: